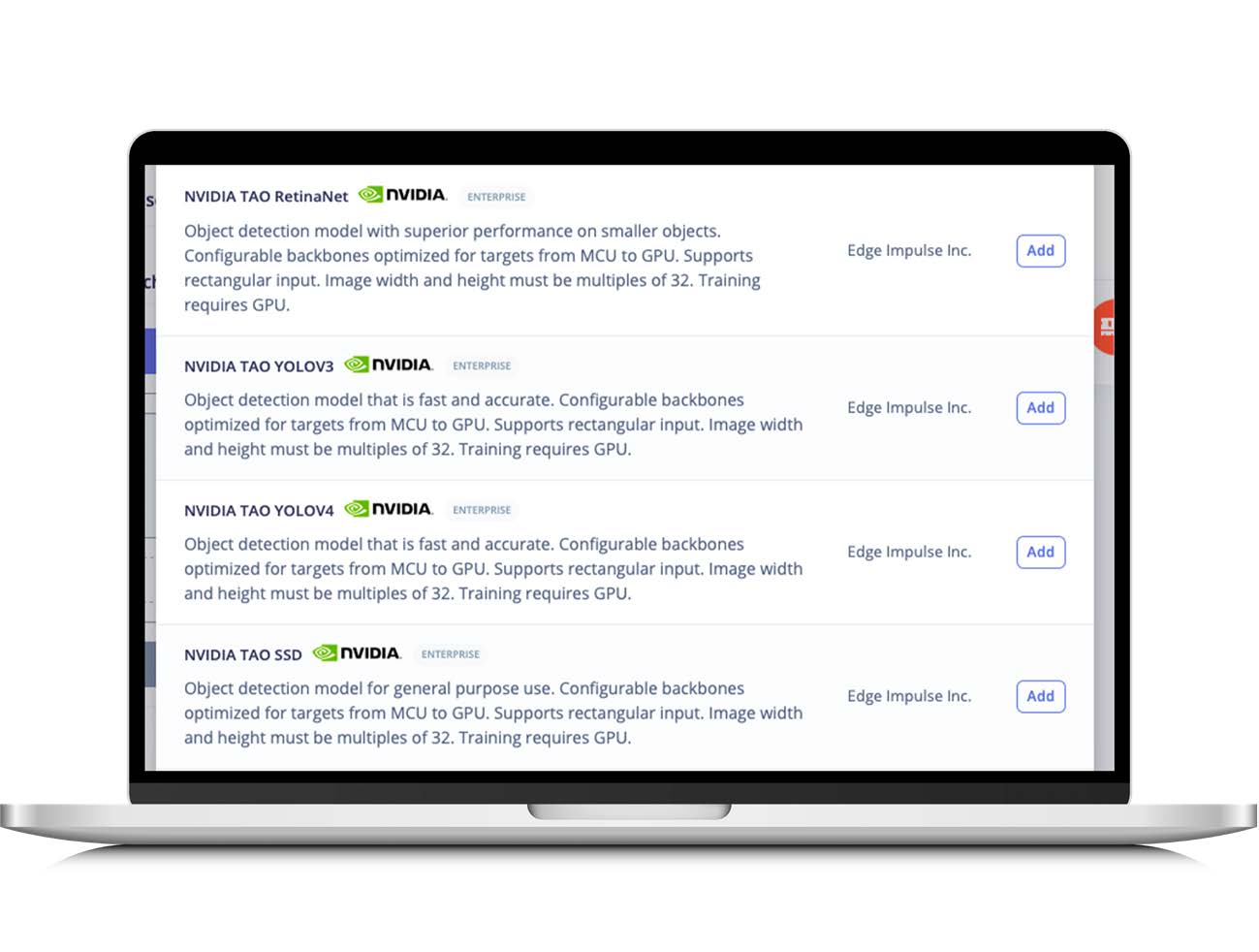
Deploying NVIDIA TAO Models on Alif Hardware With Edge Impulse
Introduction The NVIDIA TAO toolkit enables embedded engineers to use established and trained Machine Learning (ML) models and modify them slightly to better fit a particular application. This ability allows users to leverage a large library of model architectures for image classification, object detection, and segmentation as well as various task-based models without creating complex
Read More